- Get link
- X
- Other Apps
Featured post
- Get link
- X
- Other Apps
Last week, the notorious Shadow Brokers hackers group that claimed to have stolen the hacking tools and exploits from the NSA has leaked the password for an encrypted cache of Unix hacking tools and exploits, including a remote root zero-day exploit for Solaris OS and the TOAST framework.
Today the Shadow Brokers group has released another piece of the precious archive alleged stolen to the NSA, a 117.9 MB encrypted dump, it includes three folders named Windows, Swift, and OddJob including 23 new hacking tools.
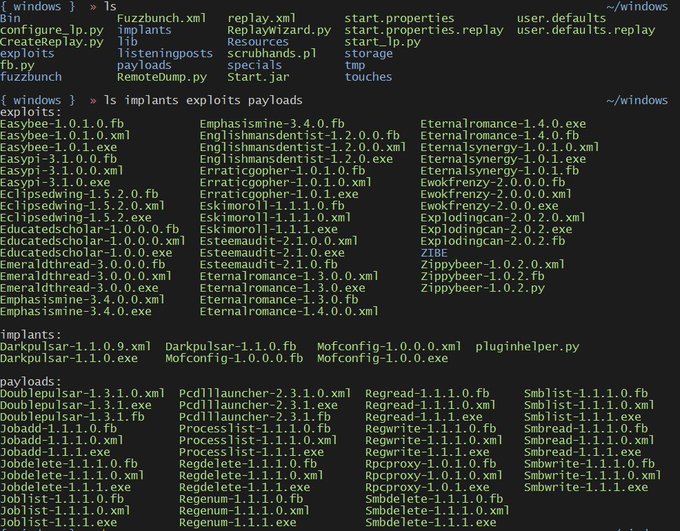
Some of the codenames for the hacking tools in the archive are OddJob, EasyBee, EternalRomance, FuzzBunch, EducatedScholar, EskimoRoll, EclipsedWing, EsteemAudit, EnglishMansDentist, MofConfig, ErraticGopher, EmphasisMine, EmeraldThread, EternalSynergy, EwokFrenzy, ZippyBeer, ExplodingCan, DoublePulsar.
The tools and exploits released today have been specifically designed to target earlier versions of Windows operating system, this last bunch of documents suggests the NSA was targeting the SWIFT banking system of several banks around the world.
The hackers published a blog post titled “Lost in Translation,” which included a link to the archive and the password.
“Follow the links for new dumps. Windows. Swift. Oddjob. Oh you thought that was it? Some of you peoples is needing reading comprehension.
https://yadi.sk/d/NJqzpqo_3GxZA4
Password = Reeeeeeeeeeeeeee
Password = Reeeeeeeeeeeeeee
” reads the blog post.
The overall archive was now available on GitHub, including the last portion.
Of course, security researchers immediately started digging the precious trove of files.
Windows exploits, payloads and implants of #EquationGroup dumped by the #ShadowBrokers: confirmed.
EMERALDTHREAD is an exploit (unpatched?) for Windows XP to Windows 2003 SP2.
The hacking tools in the Windows folder work against older versions of Windows (Windows XP) and Server 2003.
The folder OddJob contains a Windows implant and includes alleged configuration files and payloads, also in this case targeted versions are older ones like Windows Server 2003 Enterprise up to Windows XP Professional.
According to the Security expert Kevin Beaumont, who analyzed the dump, some of the Windows exploits were able to avoid detection.
So far the first 3 exploits in Windows/Exploits haven't been on VirusTotal before, nor in Palo-Alto Autofocus.
But the SWIFT folder contains a PowerPoint document that could reveal a disconcerting reality. The PPT contains credentials and data on the internal architecture of EastNets, one of the largest SWIFT Service Bureau in the Middle East.

The folder includes SQL scripts that could be used to query Oracle Database to obtain a wide range of information, including the list of users and the SWIFT message queries.

The folder also contains Excel files that demonstrate the NSA’s linked Equation Group had hacked many banks worldwide, most of them in countries in the Middle East (i.e.UAE, Kuwait, Qatar, Palestine, and Yemen).
SWIFT Host of Palestinian Bank was running Windows 2008 R2 vulnerable to exploit framework FUZZBUNCH. #ShadowBrokers cc @hackerfantastic
But EastNets’ CEO has denied NSA hackers ever compromised the systems of the company.
“The reports of an alleged hacker-compromised EastNets Service Bureau (ENSB) network is totally false and unfounded,” EastNets’ CEO Hazem Mulhim told Motherboard in an email. “The EastNets Network internal Security Unit has ran a complete check of its servers and found no hacker compromise or any vulnerabilities.” reads the official statement issued by the company.





Comments
Post a Comment